Geeks for Geeks Draw a Circle

What is the Idea Algorithm?
Thought (International Data Encryption Algorithm) is an encryption algorithm. It is a symmetric block zero that takes 64 flake as an input, 28-bit fundamental and performs 8 identical rounds for encryption in which six different subkeys are used, and iv keys are used for output transformation.
Understanding IDEA Algorithm
- The typical block size is sixteen bytes of 128 bits. A block cipher will typically operate in round blocks where function of the key is practical to the round, and then other operations are performed on it. Subsequently a certain number of rounds, say between 10 to 16, we end up with our ciphertext for that block.
- The ciphertext cake is exactly the same size every bit the plain text cake, 16 bytes. We operate on the block for each round using a function of the encryption key that we telephone call as the round key. We derive the multiple round keys from the encryption primal using a key schedule.
- The key schedule is an algorithm that Shifts, XORs, Multiplies and performs other types of operation on the original encryption key in order to come up with these round keys. Well, if I have a 16-byte block and I have a 128-bit key, which is as well sixteen bytes,
Confusion and Improvidence
Allow's understand the difference betwixt Confusion and Diffusion.
Confusion
- Defoliation has to do with the relation between key and ciphertext.
- Nosotros ensure that a modest alter in the key leads to a large change in the ciphertext.
- XOR is not sufficient; one-to-1.
- Key Schedule.
Diffusion
- Diffusion has to do with the relation between the message and ciphertext.
- A minor modify in the bulletin -> big modify in the ciphertext.
- Hides patterns within the bulletin.
So Electronic Code Book fashion of functioning, we volition usually run a block cipher in Nothing Cake Chaining mode of operation or CBC. With cipher cake chaining, you will XOR the previous block's ciphertext with the previous block's with the side by side cake's apparently text before you were encrypted. In that manner, every block in the message depends upon all of the blocks that came earlier.
Information Encryption Standard (DES)
Allow's expect at some of the aspects of the Data Encryption Standard (DES).
Key Length
- 64-scrap input
- viii-scrap parity check
- 56-fleck constructive key
Weakness
- Theoretical
- Short central
Understanding Thought Algorithm in Particular
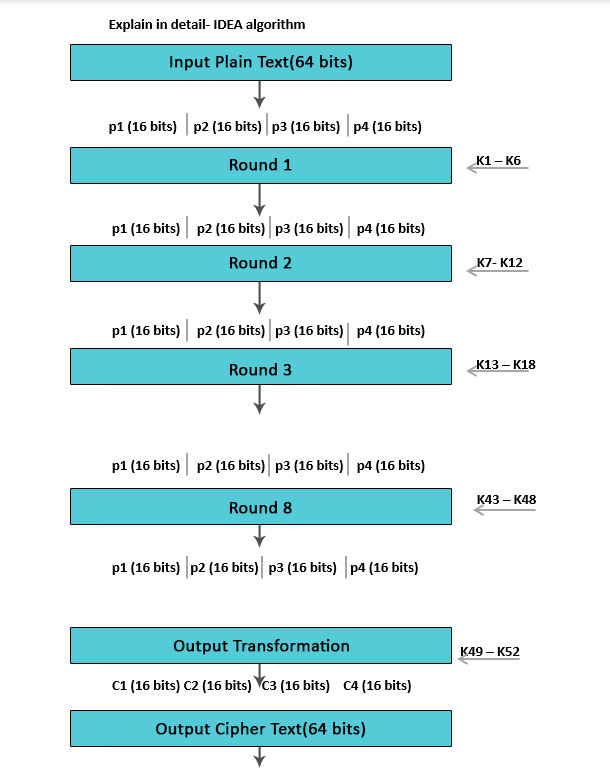
The 64-bit input patently text block-divided into 4 function (16 bits each) Declare p1 to p4.
- Therefore, p1 to p4 volition be the inputs for the initial round of the algorithm.
- At that place are 8 such rounds.
- The key is made up of 128 $.25.
- In each circular, 6 sub-keys volition be produced.
- Each one of the sub-keys includes 16 bits.
- All these sub-keys will be put on the 4 input blocks p1 to p4.
- The concluding deportment include Output Transformation, which usually benefits just 4 sub-Keys.
- The last issue is iv blocks of ciphertext C1 to C4 (each of 16 $.25).
- They are mixed to create the last 64-bit ciphertext block.
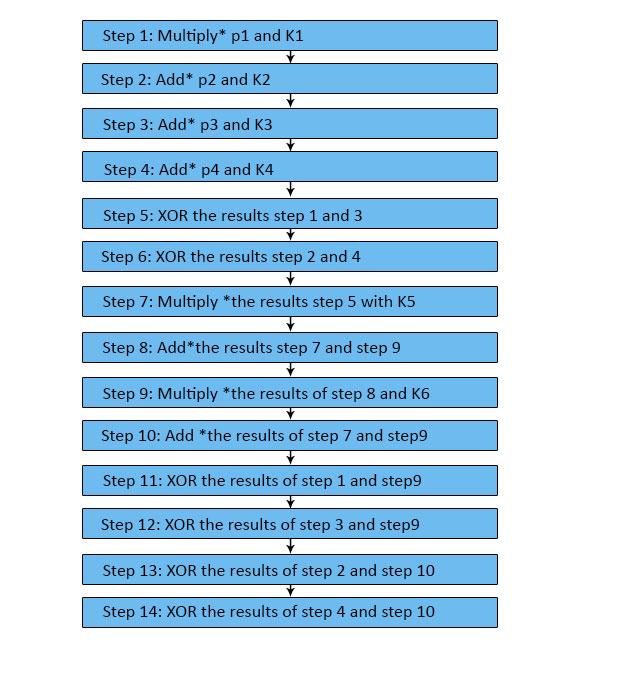
Unmarried Round Information
- There are 8 rounds in IDEA.
- Every single requires several operations around the four data blocks applying 6 keys.
- These steps work in numerous mathematical activities.
- There are multiple *, add * & XOR procedures.
- Multiply * means multiplication modulo.
- Add* requires improver modulo.
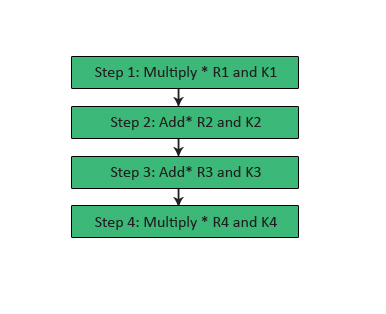
Output Transformation
- It tin can be a one-time procedure.
- It requires places by the end of the eighth round.
- The Output transformation input is a 64-bit value divided into iv sub-blocks (land R1 to R4 every among 16 bits).
- The four 16 bits Sub-keys (K1 to K4) are used here.
- The process of the outcome transformation tin exist as follows.
Determination
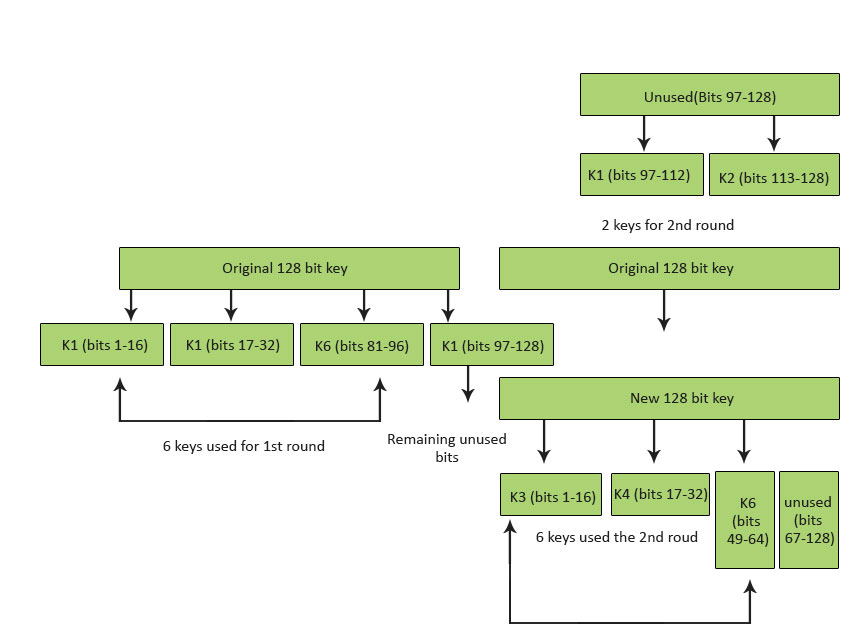
- Idea may be a recognized zip that many experts have examined for the previous ten Sub-cardinal creation for the round, each one of the 8 rounds utilizes half dozen sub-keys (hence 8 * half dozen = 48 sub-keys are essential for the rounds). The concluding result transformation benefits 4 sub-keys (i.eastward. 48 + 4 = 52 sub-keys total). From an input key 128 bits, all these 52 sub-keys will exist produced years, every bit well as; however, no strike against v or higher of its viii.five rounds has been found.
- Because of its toughness against cryptanalytic attacks and because of its inclusion in several well-known cryptographic deals, IDEA tin can be trusted. The Basic Thought algorithm is definitely not, which tin can be likened for effectiveness or security with simple DES or AES versions. The Basic IDEA algorithm is intended to assistance learners in being familiar with the Idea algorithm by giving a version of IDEA that enables instances to become worked well manually and to offer a comparison of the technique of IDEA and the ways of DES and AES.
Recommended Articles
This has been a guide to the IDEA Algorithm. Here we discussed the Idea Algorithm's understanding, data encryption standard, and the departure betwixt confusion and diffusion of the Idea algorithm. You tin can also go through our other suggested articles to learn more –
- Chiliad- Means Clustering Algorithm
- Naive Bayes Algorithm
- Ray Tracing Algorithm
- What is a Greedy Algorithm?
bardonschistermin1948.blogspot.com
Source: https://www.educba.com/idea-algorithm/